On this page
key
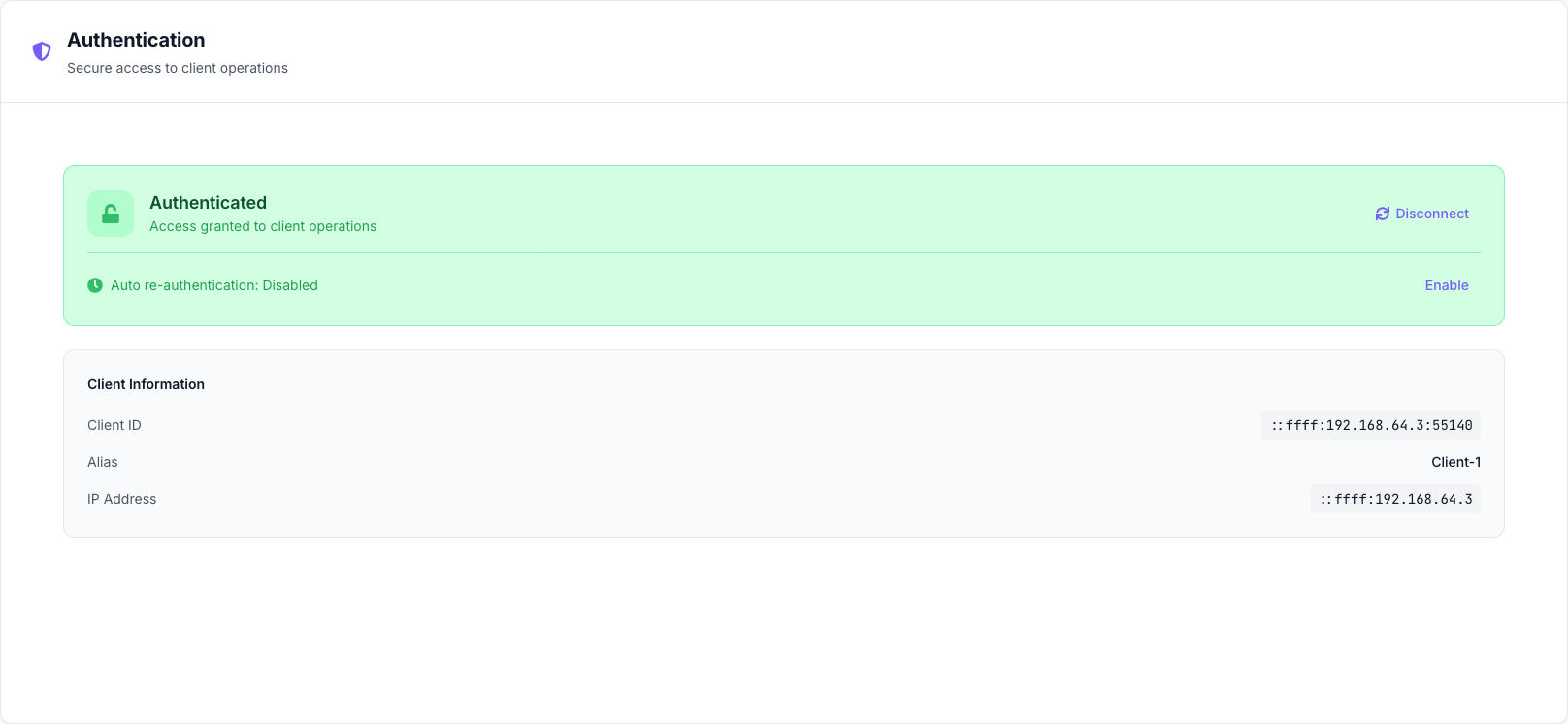
Authentication Panel
Client authentication management and security interface
How It Works
The authentication system has two layers:
- Web UI Login: JWT authentication to access the C2 interface
- Client Authentication: Per-client password authentication for rootkit control
Client Authentication Process
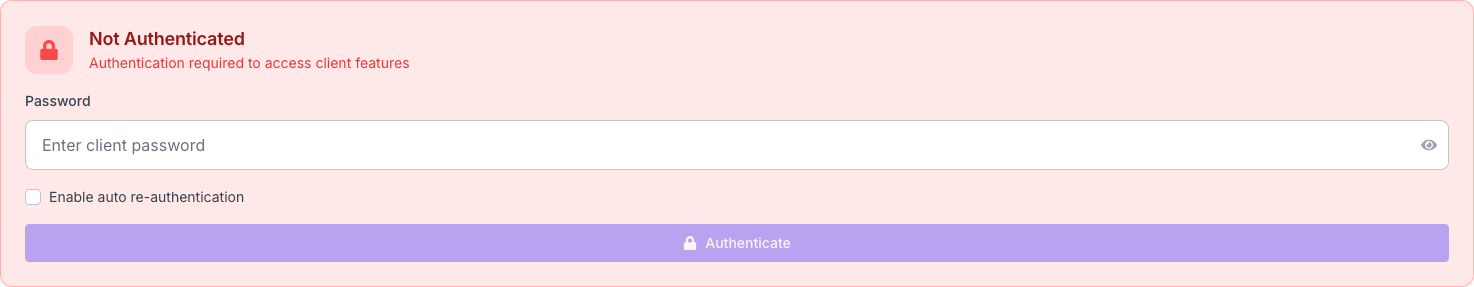
When you click “Authenticate” on a client card:
- Modal opens: Password input dialog appears
- Credential submission: Password sent to rootkit client via C2 server
- Rootkit verification: Client validates password against stored hash
- Session establishment: Authenticated session created for client operations
Security Features
- Password hashing: SHA-512 verification on client side
- Session timeout: Authentication expires after inactivity
- Per-client auth: Each client requires individual authentication
- Failed attempt tracking: Monitor and log authentication failures
- Secure transmission: Encrypted credential transfer via C2 channel